
下载APP

【单选题】


(67)应选入()
A.cr
B.security
C.favorable
D.excellent
A.
NAC’s (Network Access Control) role is to restrict network access to only compliant endpoints and (66) users. However, NAC is not a complete LAN (67) solution; additional proactive and (68) security measures must be implemented. Nevis is the first and only comprehensive LAN security solution that combines deep security processing of every packet at 10Gbps, ensuring a high level of security plus application availability and performance. Nevis integrates NAC as the first line of LAN security (69) . In addition to NAC, enterprises need to implement role-based network access control as well as critical proactive security measures—real-time, multilevel (70) inspection and microsecond threat containment.
题目标签:选入
举报
参考答案:


参考解析:




刷刷题刷刷变学霸
举一反三

【单选题】(74)应选入() A.content B.position C.power D.capacity
A.
Virtualization is an approach to IT that pools and shares (71) so that utilization is optimized and supplies automatically meet demand. Traditional IT environments are often silos, where both technology and human (72) are aligned around an application or business function. With a virtualized (73) , people, processes, and technology are focused on meeting service levels, (74) is allocated dynamically, resources are optimized, and the entire infrastructure is simplified and flexible. We offer a broad spectrum of virtualization (75) that allows customers to choose the most appropriate path and optimization focus for their IT infrastructure resources.
【单选题】(5)应选入()。 A.D<C B.R.D<S.C C.R.D<R.C D.S.D<R.C
A.
若有关系R (A,B,C,D)和S(C,D,E),则与表达式π3,4,7(σ4<5(R×S))等价的SQL语句如下:
B.
SELECT (3) FROM (4) WHERE (5) ;
C.
【单选题】(30)应选入() A.understand B.dislike C.study D.excuse
A.
Michael Greenberg is a very popular New Yorker. He is not famous in sports or the arts, But people in the streets 16 him, especially those who are 17 . For those people, he is "Gloves" Greenberg. How did he get that 18 He looks like any other businessman, wearing a suit and carrying a briefcase (公文箱). But he’s 19 . His briefcase always has some gloves。 In winter, Mr.Greenberg does not 20 like other New Yorkers, who look at the sidewalk and 21 the street. He looks around at 22 .He stops when he 23 someone with no gloves. He gives them a pair and then he 24 ,looking for more people with cold 25 . On winter days, Mr.Greenberg 26 gloves. During the rest of the year, he 27 gloves. People who have heard about him 28 him gloves, and he has many in his apartment. Mr. Greenberg 29 doing this 21 years ago. Now, many poor New Yorkers know him and____30____his behavior. But people who don’t know him are sometimes 31 him. They don’t realize that he just wants to make them 32 . It runs in the 33 .Michael’s father always helped the poor as he believed it made everyone happier. Michael Greenberg feels the 34 .A pair of gloves may be a 35 thing, but it can make a big difference in winter.
【单选题】(41)应选入() A.5.4 B.5.6 C.7.4 D.7.6
A.
已知某拟建项目财务净现金流量如下表所示,则该项目的静态投资回收期是 (41) 年。进行该项目财务评价时,如果动态投资回收期Pt小于计算期n,则有财务净现值 (42) 。
B.


【单选题】(17)应选入()。 A.together B.by themselves C.separately D.alone
A.
Extreme Programming (XP) is a discipline of software development with (14) of simplicity, communication, feedback and courage. Successful software development is a teameffort - not just the development team, but the larger team consisting of customer,management and developers. XP is a simple process that brings these people together andhelps them to succeed together. XP is aimed primarily at object-oriented projects using teamsof a dozen or fewer programmers in one location. The principles of XP apply to any (15) project that needs to deliver quality software rapidly and flexibly.
B.
An XP project needs a(an) (16) customer to provide guidance. Customers, programmers, managers, are all working (17) to build the system that’sneedeD. Customers - those who have software that needs to be developed - will learn simple,effective ways to (18) what they need, to be sure that they are getting what they need,and to steer the project to success.
【单选题】(4)应选入()。 A.R B.S C.R,S D.RS
A.
若有关系R (A,B,C,D)和S(C,D,E),则与表达式π3,4,7(σ4<5(R×S))等价的SQL语句如下:
B.
SELECT (3) FROM (4) WHERE (5) ;
C.
【单选题】(58)应选入()。 A.1→2 B.2→1 C.3→2 D.2→4
A.
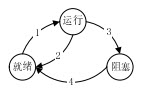
某系统的进程状态转换如下图所示。图中1、2、3和4分别表示引起状态转换时的不同原因。原因4是由于 (57) ;一个进程状态转换会引起另一个进程状态转换的是 (58) 。
B.

【单选题】(75)应选入() A.solutions B.networks C.interfaces D.connections
A.
Virtualization is an approach to IT that pools and shares (71) so that utilization is optimized and supplies automatically meet demand. Traditional IT environments are often silos, where both technology and human (72) are aligned around an application or business function. With a virtualized (73) , people, processes, and technology are focused on meeting service levels, (74) is allocated dynamically, resources are optimized, and the entire infrastructure is simplified and flexible. We offer a broad spectrum of virtualization (75) that allows customers to choose the most appropriate path and optimization focus for their IT infrastructure resources.
【单选题】(66)应选入() A.automated B.distinguished C.authenticated D.destructed
A.
NAC’s (Network Access Control) role is to restrict network access to only compliant endpoints and (66) users. However, NAC is not a complete LAN (67) solution; additional proactive and (68) security measures must be implemented. Nevis is the first and only comprehensive LAN security solution that combines deep security processing of every packet at 10Gbps, ensuring a high level of security plus application availability and performance. Nevis integrates NAC as the first line of LAN security (69) . In addition to NAC, enterprises need to implement role-based network access control as well as critical proactive security measures—real-time, multilevel (70) inspection and microsecond threat containment.
【单选题】(67)应选入() A.crisis B.security C.favorable D.excellent
A.
NAC’s (Network Access Control) role is to restrict network access to only compliant endpoints and (66) users. However, NAC is not a complete LAN (67) solution; additional proactive and (68) security measures must be implemented. Nevis is the first and only comprehensive LAN security solution that combines deep security processing of every packet at 10Gbps, ensuring a high level of security plus application availability and performance. Nevis integrates NAC as the first line of LAN security (69) . In addition to NAC, enterprises need to implement role-based network access control as well as critical proactive security measures—real-time, multilevel (70) inspection and microsecond threat containment.

