下载APP

【单选题】


(71)处填()。
A.nonviral
B.unviral
C.inviral
D.abviral
A.
Remote administration types are an example of one kind of (71) malicious software, the Trojan horse, or more simply Trojan. The purpose of these programs isn’t replication, (72) to penetrate and control. That masquerade as one thing when in fact they are something else, usually something destructive. There are a number of kinds of Trojans, including spybots, (73) report on the Web sites a computer user visits, and keybots or keyloggers, which record and report the user’s keystrokes in order to discover passwords and other confidential information.
B.
RATS attempt to give a remote intruder administrative control of an infected computer. They work as (74) pairs. The server resides on the infected machine, while the resides elsewhere, across the network, where it’s available to a remote intruder. Using standard TCP/IP or UDP protocols, the sends instructions to the server. The server does (75) it’s told to do on the infected computer.
题目标签:处填
举报
参考答案:


参考解析:




刷刷题刷刷变学霸
举一反三

【单选题】(70)处填()。 A.access B.accessing C.assert D.asserting
A.
You want to use the Web to let Eternal users or your customers look at corporate information. But you want to keep installation at the user end (66) and you don’t want just anyone to get (67) your databases.
B.
That may be where an application server enters the picture. For more user machine independent, these t software packages, typically written in the (68) programming language.
C.
for use on Windows NT-based systems, act as go-betweens linking browser-equipped end users to the databases that (69) the information they need to (70) 。
【单选题】(64)处填()。 A.488888 B.388888 C.288888 D.188888
A.
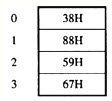
高速缓存Cache与主存间采用全相连地址映像方式,高速缓存的容量为4MB,分为4块,每块1MB,主存容量为256MB。若主存读写时间为30ns,高速缓存的读写时间为3ns,平均读写时间为3.27ns,则该高速缓存的命中率为 (63) %。若地址变换表如表1-6所示,
B.
表1-6 地址变换表
C.

D.
则主存地址为8888888H时,高速缓存地址为 (64) H。
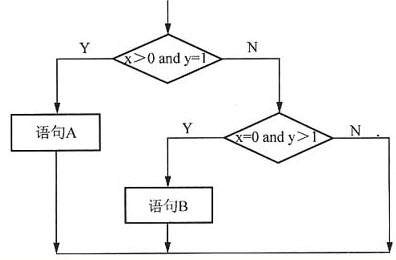
【单选题】(71)处填()。 A.(5*1+2+3+6)/8 B.(5*1+2+3+6)/9 C.(8*1)/8 D.(8*1)/9
A.
已知一个线性表(16,25,35,43,51,62,87,93),采用散列函数H(Key)=Key mod 7将元素散列到表长为9的散列表中。若采用线性探测的开放定址法解决冲突(顺序地探查可用存储单元),则构造的哈希表为 (70) ,在该散列表上进行等概率成功查找的平均查找长度为 (71) (为确定记录在查找表中的位置,需和给定关键字值进行比较的次数期望值称为查找算法在查找成功时的平均查找长度)。
【单选题】(58)处填()。 A.a、b、c、d、e B.e、d、c、b、a C.c、d、b、a、e D.e、a、b、d、c
A.
设栈S和队列Q的初始状态为空,元素按照a、b、c、d、e的次序进入栈S,当一个元素从栈中出来后立即进入队列Q。若队列的输出元素序列是c、d、b、a、e,则元素的出栈J顷序是 (58) ,栈S的容量至少为 (59) 。
【单选题】(3)处填()。 A.5590 B.5595 C.6000 D.6007
A.
若每一条指令都可分解为取指、分析和执行三步。已知取指时间为5△t,分析时间为2△t,执行时间为5△t。如果按顺序方式从头到尾执行完500条指令需 (3) 。如果按[执行]k、[分析]k+1、[取值]k+2重叠的流水线方式执行,从头到尾执行完500条指令需 (4) △t。
【单选题】(6)处填() A.unwieldy B.tough C.tamable D.invaluable
A.
Like many other aspects of the computer age, Yahoo began as an idea, (1) into a hobby and lately has (2) into a full-time passion. The two developers of Yahoo, David Filo and Jerry Yang, Ph.D. candidates (3) Electrical Engineering at Stanford University, started their guide in April 1994 as a way to keep (4) of their personal interest on the Internet. Before long they (5) that their homebrewed lists were becoming too long and (6) Gradually they began to spend more and more time on Yahoo.
B.
During 1994, they (7) yahoo into a customized database designed to (8) the needs of the thousands of users (9) began to use the service through the closely (10) Internet community. They developed customized software to help them efficiently locate, identify and edit material stored on the Internet.
【单选题】(7)处填() A.addresses B.sites C.places D.spaces
A.
When the subject is money, women often cling to two persistent stereotypes, one a pleasant dream, the other a nightmare.
B.
In the (1) , they hate fantasies that a white (2) will provide happily-ever-after financial security. (3) the nightmare, by contrast, they fear that an impoverished retirement could (4) them into bag ladies on the street.
C.
Now (5) advisers and managers are (6) forces to change those images. In a proliferation of books, seminars, conferences, Web (7) , and investment clubs, they are (8) out to women, helping them to become financially savvy and economically (9) . Prince Charming, they warn, may not come.
D.
"If and when he does show (10) , he may have less than you do," quips Brooke Stephens, a financial adviser.
【单选题】(69)处填()。 A.1NF B.2NF C.3NF D.BCNF
A.
设有关系模式S(Sno,Sname,Pno,Pname,Q,A)表示销售员销售商品情况,其中各属性的含义是:Sno为销售员员工号,Sname为销售员姓名,Pno为商品号,Pname为商品名称,Q为销售商品数目,A为销售商品总金额,根据定义有如下函数依赖集:P=Sno→Sname,Sno→Q,Sno→A,Pno→Pname
B.
关系模式S的关键字是 (66) ,W的规范化程度最高达到 (67) 。若将关系模式S分解为3个关系模式S1(Sno,Sname,Q,A),S2(Sno,Pno,Pname),则S1的规范化程度最高达到 (68) ,S2的规范化程度最高达到 (69) 。
C.
SQL中集合成员资格的比较操作“元组IN(集合)”中的“IN”与 (70) 操作符等价。
【单选题】(28)处填()。 A.O(n) B. C.O(n2) D.O(1)
A.
计算N!的递归算法如下,求解该算法的时间复杂度时,只考虑相乘操作,则算法的计算时间T(n)的递推关系式为(27);对应时间复杂度为(28)。
B.
int Factorial(int n)
C.
//计算n!
D.
if(n<=1)return 1;
E.
else return n * Factorial(n-1);